Encryption is not a new concept, in fact its been around since the dawn of civilisation. The 1st Century Roman army used encryption techniques to hide military messages from enemies and indeed every noted empire since has used encryption for one purpose or another.
Perhaps the most famous form of encryption on most people’s conscious is that of the German Enigma coding machines used in the 2nd world war. The allies famously gained access to the transmitted information on these machines through the brilliant work done at Bletchley Park during WW2
But what is Encryption ?
In essence encryption is merely the practice or method of hiding information so it cannot be easily understood or digested without having the ‘key’ to unlocking that information.
When we talk about encryption we really mean data encryption specific to modern computing but the principle remains, taking plain easy to understand data and ‘encrypting’ the data so that it becomes un-readable and therefore in-accessible to all but those who have the ‘key’
Modern computer encryption works by utilising decryption algorithms either stored externally or via hidden partitions. Additional logic checks are often performed at boot up for additional security.
We are big fans of Bitlocker computer encryption here at The Red Penguin Group Ltd because it offers all the advanced features you require from encryption and best of all its included free and pre-installed with Windows 10 Pro / Enterprise and Education. Its not included in Windows 10 Home and its also not as easy to setup in Windows 7 however given the end of life status of Windows 7 you should not be using that anyway – Check out our blog for more info on Windows 7 end of life.
Password protection is NOT encryption
Its worth pointing this out, password protecting a computer or file does not encrypt its contents. Encryption protects the file no matter where the file is accessed from, by password protecting a file or computer you are simply blocking access for a given user , In essence password protection for computer files and folders can be bypassed quite easily through various techniques and permission alteration.
A typical example of this. Lets say you password protected your login to your laptop. Lets say someone stole your laptop and wanted to access the data within , that person is almost certainly not going to waste time trying to guess your password instead they are going to just remove the hard drive that contains the data and plug into another computer and then take ownership of its contents.
Microsoft Bitlocker – Built in Windows encryption

Microsoft Bitlocker is a free native app (built in) within Windows 10 Pro / Education and Enterprise versions of Windows. It offers users the chance to encrypt either their entire start up disk (hard drive) or certain folders.
Typically most users choose to encrypt their entire hard drive thus preventing access to all data in the event of computer loss. For this to work Bitlocker requires 2 HDD partitions (typical Win 10 setup) namely the system partition and the main OS partition. The Bitlocker system encrypts your OS partition as this is where your data is stored. It also requires the use of a TPM module which is a physical element of your computer’s motherboard that contains cryptographic key securing firmware. Almost all modern Windows based computers will have a TPM module available.
In a nutshell after your OS partition has been encrypted and secured against a encryption key then this data can only be accessed once your computer has completed its boot up integrity check – This is where the TPM does its stuff. During boot up your TPM checks the non-encrypted system partition and references key metrics about the computer (hardware / Boot up device etc) and if the boot up environment is different to what it was expecting the OS encrypted data remains in-accessible. This is what stops someone from taking your hard drive and trying to gain access. In the event your stolen data needed decrypting outside your computer then the decryption key would be required.
Given a typical encryption key looks like this 56248-754888-568991-563214-776512-665895-222574-132248 its safe to say nothing or no-one is going to ‘guess’ this key.
Because the encryption process runs before bootup once you have booted into your Windows performance remains the same and because encryption is done on the entire OS drive anyone who logs in will automatically be encrypted.
We can help setup computer encryption helping ensure your data stays in the right hands, Get in touch today.
What about file encryption ?
So maybe you don’t want to encrypt your entire OS partition (we can’t think of a reason not too) or maybe you also want to add another layer of encryption for your computer? In that case you will probably be interested to learn about EFS (Encrypting File System), this is the process by which you secure files or folders within a computer behind an encryption process.
This system essentially encrypts a file using a symmetric key, the symmetric key is then encrypted with a public key associated with the user account of the person who initially encrypted the file.
EFS is supported on NTFS based computers, within the Windows platform everything from Windows 2000 can support EFS.
In practice users may choose to encrypt a common folder that all users have access to on that computer – It could be that the same computer is used by different staff on different days, lets say a folder on the main C: partition called FINANCES. User A who deals with payroll on a Monday encrypts this folder and they have access when they are in the office on Monday’s but for the rest of the week the sales person uses the computer. As long as the sales staff member logs in with a different user account they will not be able to access the contents of that folder.
The same is true if the folder was stored on a USB memory stick , the EFS system will check that the person accessing is the person who originally setup the encryption. We are strong advocates for EFS and having both the OS partition encrypted with Bitlocker and folders secured with EFS is key to a secure system.
2FA & SSL

Remember encryption is not just about your computer and computer files its also relevant to anywhere you store sensitive data. Given many small businesses have a online presence and often use e-commerce to ply their trade its really important to ensure your website traffic is secure. Enter SSL!
Website SSL (Secure Socket Layer) is a method of encrypting traffic between your website and the website server, by using a SSL enabled website you are making sure that all traffic from your website is securely encrypted.
You may already have this setup – The easiest way to tell if a website is SSL enabled is to check the web URL, if the URL is prefixed with HTTPS:// (rather than http://) then all good. Also you will often see a padlock again indicating a secured website. Certain browsers such as Chrome will name and shame non-SSL websites when you attempt to connect specifically with a ‘this website is not secure’ box.
Note that SSL certification & encryption is something that regularly needs renewing typically every 1-2 years.
Given users will be tempted to not use your website if its not SSL enabled its also important for business to get your SSL in check, we can secure your website with SSL quite easily and for a very small charge – Get in touch today
2FA or two-factor authentication is something a bit different but equally as important in the fight to remain data safe. In essence its the practice of enabling a secondary authentication method to certain things like email login or cloud storage (Google Drive / Dropbox etc) ensuring that only the authenticated user gains access. 2FA works alongside encryption to offer robust protection to your data.
In a typical 2FA enabled scenario lets say you have your Gmail/365 account hacked and someone gets your password, when that hacker tried to access your Gmail/365 account from their device then before they could access your email from this unknown device the authenticated user (i.e. you) would be required to give the go ahead first. Typically this is in the form of a smartphone app pop up on the authenticated user’s phone like this:
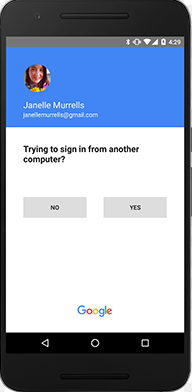
By utilising SSL certification , 2FA for storage and email accounts and encrypting your laptop or computer you will be well on your way to having a secure setup. Combine this with up to data enterprise grade Anti-Virus, Anti Spam email protection and a well designed backup system then you are off to the races!
Don’t have the skill-set or time to sort all this out?
That’s where we come in – Our managed IT support solutions take all the stress away from you – We will get everything setup and ticking along for you, sort your encryption out and get you protected. You pay a transparent small monthly fee (between £19-£30 per month) and we do all this stuff and much more besides for you and given all of our managed IT support packages come with UNLIMITED remote and phone support you can say goodbye to large ad-hoc IT bills.
As always if you feel our hints and blogs have helped then give us a like on Facebook , twitter , LinkedIn or Google or check out our website to see what we do and how we can help

